In order to pull the birthers’ chain and to contribute to a sense of community, Obots use the word “sekrit” instead of “secret.” I was reminded of secrecy when I read the article over at the Oh, For Goodness Sakes! blog that mentioned a birther project called “White Rose.” Like something in a chain email, it’s probably fantasy rather than real. The birthers had a lot of fun passing the story around, though. Squeeky Fromm did a hilarious look at the thing on the Birther Think Tank blog.
The part that I want to focus on is this:
Working over the last several months, using information already gleaned by other investigators and communicating via encrypted email and private social networks, the group has pieced together a web of conspirators including members of the legal profession, the IT community, journalists, web bloggers, Obama operatives and government officials.
I’ve never bothered much with encryption except for the KeePass program I have on my flash drive where I store passwords. Encryption seems more trouble than it’s worth for most things. When I was working, I transported protected health information (including medical records of AIDS patients) and vital records, and when doing that one must be responsible in handling other people’s information, and so of course I encrypted these files heavily.
There is strong encryption and weak encryption. Tools on the Internet will crack (read without the password) many PDF files that use PDF encryption. Some protection that office productivity programs provide when saving a file are easily cracked too. If you rely on any encryption scheme, read up on it first to see how strong it is.
I wanted to mention a few strong encryption options, should you need that type of security. I’m a Microsoft Windows user, so those are what I’m talking about, although some of these are available on other platforms.
TrueCrypt
Update: TrueCrypt is no longer maintained and may have vulnerabilities. For Windows disk encryption, use Bitlocker. Other alternatives here.
TrueCrypt is a really excellent program that creates an encrypted partition on your computer or external flash drive. It comes with some educational material. You do have to have administrator authority on the computer where you run the program, a problem if you were to try to run it on a public computer (but doing anything secret on a public computer is a bad idea anyway).
KeePass
KeePass is a simple password manager. It can run without installation, making it eminently suitable for running from a flash drive. You can arrange your passwords and notes in folders with a search capability. I’ve used it for years. There’s an iPhone version.
7-Zip
7-Zip, like WinZip, PKZip and other similar programs, is basically a compression utility. It can take files or folders and combine them into a single smaller (often much smaller) file. Optionally it can encrypt the files at the same time. The 7-zip encryption is strong (choose the AES option) and the program runs fast. I’ve used it commercially on multi-gigabyte databases.
Email Solutions
Up until now, all of the solutions I’ve mentioned use what are called symmetric keys. That just means that you use the same key to write the encrypted data that you use to read it. Such solutions are useful when you have something that you want only yourself to be able to see, or a trusted partner that you can send the key to. The tricky part, of course, is sending that key securely over long distances.
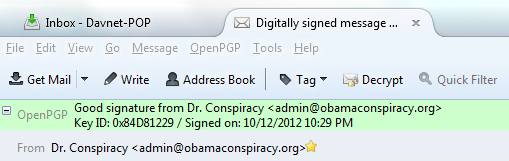
An elegant solution is an asymmetric algorithm. In these “public key cryptosystems” one key encrypts the file and the other one decrypts it. One key is called a “public key” and the other a “private key.” With this approach, I can publish my public key to the world, and then anyone can use it to encrypt something directed to me that only I, with my private key, can read. It’s a very elegant solution. Public key cryptosystems can also be used to verify the sender of a communication. If I encrypt something with my private key, anyone can read it with my public key, meaning anyone can be sure it’s authentic from me, and not altered in transmission. Several email clients can use GnuPG, an implementation of a public key system. I use Thunderbird as my mail client and have for over a decade. It has an add-in called Enigmail for sending and receiving encrypted emails. There is a nice tutorial on how all this fits together. Note that the encryption of emails conforms to standards, so one can use a variety of programs to exchange encrypted correspondence. Here’s what an authentic digitally signed message looks like in the Thunderbird email client:
One of the cool things Enigmail does for you is to allow you to publish your public key to an Internet server. The public correct key is identified by your email address. For example, if you send an email to this web site to the “admin” user, Enigmail can find the public key automatically. You can also send the keys in a file. My public key is pasted at the bottom of this article.
Encryption can be a hassle, and encrypted emails require some effort to set up. Most folks really don’t need it, but if you do, there are freely available tools at no cost. If you find one of these tools useful, seriously consider contributing to the author.
How strong are these algorithms? You can probably find something on the Internet. Also check out Bruce Schneier’s excellent security blog (just be aware that today is Friday and on Fridays he blogs about squid).
Final note: if it’s worth encrypting, it’s worth a nice long random password. I use a 24-character random string for my KeePass password file.
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v2.0.17 (MingW32)
mQENBFB4qf0BCACqpQlqmVnSG4KpSRzTSXsuWLdKRxqYj5MTW2IfxWlmT9tmbfha km3oNzidofKV7qc/fA0/SYYjC+wHezxmLlohpfhcjFYJ9U+oIpigg1/THC5zUtmp QYhq0bw8t17nOydVqgC9f+ag+QiyF4zpd957ad9c9R+ayA67p1DC88V3wHsixSI7 3tc1Knk/hG0baQdMr/clZkNZF9s5erXZ26bFfh8/JOCSv98qdc2ng4A4yEzcyZte bgCpmeDDiFHwI3AXIJjW9ecTgFf4pkY66dwVyTbLDf6s0egSr9r6qgF9ZsECsJip y8RFrUWed8oIxOY1aNkk5M7dauTZB7Eo8UHzABEBAAG0KkRyLiBDb25zcGlyYWN5 IDxhZG1pbkBvYmFtYWNvbnNwaXJhY3kub3JnPokBPgQTAQIAKAUCUHip/QIbIwUJ CWYBgAYLCQgHAwIGFQgCCQoLBBYCAwECHgECF4AACgkQqJ0lqoTYEikoaAf+KYkL Z8MyrugMghCar7/+nfKavxQAoTrGt0feNsE+L2lZTT4fFtPWFYCB0G97u7OBaPpi gG/teqKADFptrFwGmCQePRPTsNUZh6a9sgKQgNKbbC002o/xfcNPXnBgaqm1vUAd +qA+1ZJttBvs3UyTAsG8iQ32ceNIXQRdAbubJCFCwSYL3l2gcXn40KRYE6s/L108 Wi2Rh3yQZsLyO78FYmNzIqfrvbrWeIVHEq3yb/tCPEQlz2fcywrlUcRDyYsSKVLs MYyeAn+9rUlrd3t+RFuCH/tAjf0xWXyFgeDnUNRiAXXr7Q5GVKNAUESs1eknwVTu CMGPjUsvs0Bki2KPB7kBDQRQeKn9AQgA6TPgBGQ8QYoPVNK7DIKu757pcP1xQyI9 50kFt8sqNwmePG25N/HZKKJLCe3FlU4jj0s32/3yWF9pWPTtVqtCYnD4CuJpFjMK ty8CBIrY2Q1/dwOqQ2iI0q6wP4m0rGV0fKhhVsQAu5/NheFTMFO1dd5ZRF/4D0Js J1BB5lYJkjLU9zvY4W/QJOM7ImbWyaLs6FlFj+rWK78P8sltq5UCP6FKBgxeKIKw cSOIU38PaSYWGI1gvXpxokQb6Rtl/iBB5DWR3Avv8ZL0yheLtMQIoLdbNAVPfQnl 5hu33K/wlW72cpP1lmbKvpNr/JHhhCoT6hEiXCT1Y9/6PZeO1fxFiQARAQABiQEl BBgBAgAPBQJQeKn9AhsMBQkJZgGAAAoJEKidJaqE2BIpbhEH/3u2xM9RjQSBF67c QSuV+7vGV0oU3xmrELB3cxoqgYveU6d1XjHWDyRf6evzkUS26HEKkhratowLaPTv 1V44l3NKIGiCJKv+K+LDQcCIVh/Fq7rxoc47JyFYO6MPQVyN9nh1sDslzTfswbCJ hRTsRl6TS6xlmBEL0/HMGPDQEs2lTF4uCnHeOg46pcIr7UcLr5OKMKsNnK3hdOCL tYm3MxZY/76K1SkcLTnz0A9eZm4PxvdTZftGQGeaTw1UzMEAhEHD3hab1lACI34F 9VBfweBE77sdJinW9JAfJj8MrtGma0smeXju760xwb2MIR9WjX57NPH+K77/1Qkc ui1P2/8= =r4Vx -----END PGP PUBLIC KEY BLOCK-----





why aren’t they encrypting emails by default
Emails aren’t encrypted by default because not everyone is equipped to receive them. Lots of folks use webmail to read mails, and some of those programs don’t support encryption. Also you can’t encrypt an email without knowing the recipient’s public key.
The Thunderbird client can encrypt emails by default if you tell it to, and I seem to recall that Microsoft Outlook has the same option; I know Outlook can digitally sign emails by default.
I second the Doc’s recommendation for KeePass. It is simple yet very sophisticated and under continual development. There are versions for almost any operating system you want: Windows (Win32 and DotNet), Windows Mobile, MacOS and iOS, Linux (several flavors), Android, Blackberry, PalmOS, and others. I expect the Windows 7 version to run on Windows 8 desktops with no problem, and the Windows 8 tablet version will not be far away.
KeePass can be installed on your hard disk into the registry or as a portable application. The portable application can be standalone or part of the PortableApps framework.
PortableApps is framework/menu system with hundreds of applications and utilities that can run completely independently of the Windows registry installation process. That means you can carry them around on a message stick and use them on any Windows computer that you encounter with out leaving behind installation debris. You always have your favorite programs and data files available where ever you go. There are hundreds of top of the line, world class, ‘open source’ and/or ‘free’ applications that have portable versions configured for PortableApps, including KeePass, 7Zip, GIMP, Firefox, Thunderbird, Chrome, OpenOffice and LibreOffice, and lots of Games, Security, Education, Utilities.
Doc’s recommended ‘TrueCrypt’ has a portable version too. It isn’t configured for management through the Portable Apps framework, but you can manually include it in the menu.
it would be easy and reasonable to make it the default in browsers or mail-services.
I speculate NSA etc. don’t want it. I’d read AOL gives NSA access to all my emails
for their “carnivore/omnivore” system.
USA is famous for illegally spying on EU-residents privacy, see Google,Echelon etc.
One of the products I’ve used for years is BCArchive, a free encryption archiver, which works much like 7-Zip and WinZip. http://www.jetico.com/download/
I really don’t have all that much that needs encryption, but it’s handy to have when I do need it.
As someone who’s studied a little information theory, I’ve always thought this was a very relevant (and unappreciated) comment about password security:
http://xkcd.com/936/
xkcd is quite good usually, but the sample password that is ‘hard for the computer’ isn’t really so hard, it is relatively easy to crack with a dictionary attack. even if it is four words.
add a few periods to it though and the difficulty goes through the roof
why don’t we have simple devices that safely create and enter and
store and remember passwords
We do. And Doc recommended, INT THIS POST, one that is really very good: KeePass.
Besides the ones Doc mentioned and Keith brought up, again, there is another one. You have a system to create, enter, store and remember passwords. It is located in a specific spot, above your shoulders.
I’m really surprised there’s been no mention of LastPass. It is far more integrated into browsers and Windows than KeePass. I’ve used it successfully for more than two years.
https://lastpass.com/
Did you change all your passwords after they got hacked last year?
I put my KeePass DB on dropbox and use it from all my varioius devices, desktop, laptop, phone.
KeePass has plugins for integration with IE, Firefox, and Chrome.
Here is a discussion of some KeePass versus LastPass vulnerabilities on Wilders Security Forums: KeePass – a further leap ahead
it should be integrated,automatic,default.
So that people even needn’t know what passwords,encryption is.
————–
This notebook permanently asks me to register my fingerprints,
(among many other annoying things)
I never did, dont know how,why,how long it takes,how safe/good it is,
what the trustworthy reviewers say,
If I have a GPG2 or PGP public key in my keyring, email to you is encrypted and signed automatically. I’ve been doing some version of this protocol for at least fifteen years.
I know folks that swear by those “easy” passwords shown in the cartoon, and I have never thought much of them. One time at work I turned a password cracker loose on our Windows NT server and in 10 minutes it had cracked 80% of the login passwords in the company.
My pet peeve though is requirements to change passwords frequently. One ends up either making simple passwords, or writing them down.
I have three 8-character passwords that consist of upper and lower case letters and numbers, randomly generated. For my key store, I string the three together for 24 characters. For my TruCrypt volume, I use a 16-character randomly-generated password that also includes special characters.
So there.
I use fingerprint access to my laptop. It wasn’t much trouble except when I had to wipe the OS when I Installed Windows 7 and had to find new drivers for the hardware. It still lets you login with a password, by the way, after you enable fingerprint access.
I’m going to generally hate new software,accounts,eshopping,subscriptions
these days due to their usually long and complicated terms and or licence agreements or
Amen, Doc, amen. I understand the rationale, but ultimately, I believe this does no good. Pretty much forces users into relaxing protocols.